Customer want to upload files form IoT edge to Storage account in few cases and currently as per Microsoft document File upload is not supported link for IoT edge devices. As alternative we can use storage blob modules and we can upload the files to storage account as draw back we need to provide the storage account Access key link. Security is not ok with Access keys and SAS token. I have found that we can use Azure ARC managed identity to connect the storage account
IoT Edge file upload using Azure ARC
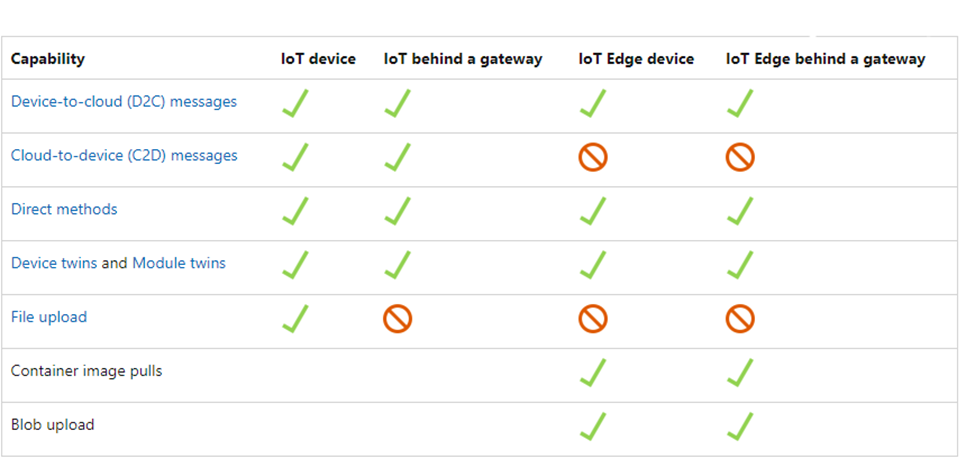
To overcome the security issues we have another solution which is Azure ARC , the advantage of Azure ARC is once we onboarded the IoT edge to azure ARC it will have managed identity using that we can provide access to storage account.
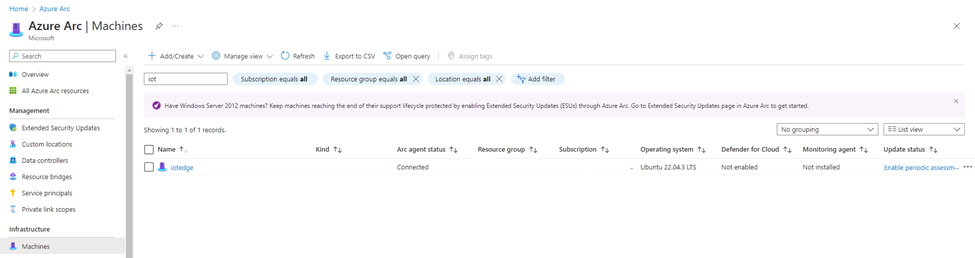
On board the machine to Azure ARC
Install the agent on the IoT edge and it will connect to Azure ARC as pre request only x86-64 (64-bit) architectures are supported
For an Azure Arc-enabled Linux server, using Bash invoke the web request to get the token from the local host in the specific port. Specify the following request using the IP address or the environmental variable IDENTITY_ENDPOINT. To complete this step, you need an SSH client.
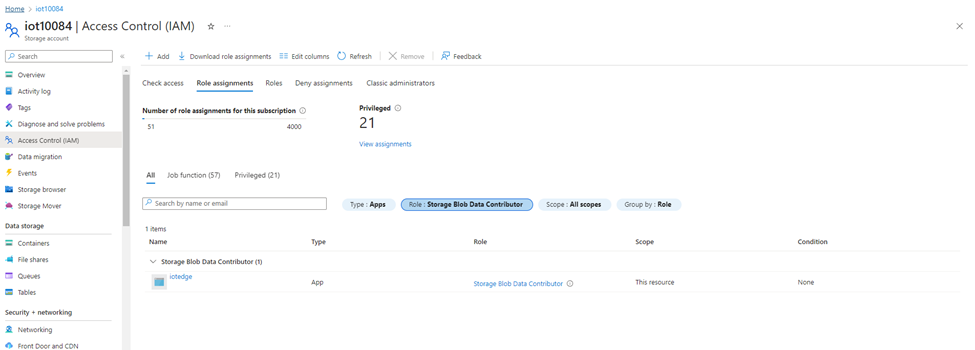
Pre request in storage account
“Storage Blob Data Contributor” role should be assigned to Azure ARC machine
Create a sample file and upload in to container to check the access from Iot edge device
Generating Access token
To connect the storage account, we need to generate the bearer token, use below token for generating the bearer token run this on sudo privilege mode and copy the bearer token in the note pad. Depends on the service which we are accessing from ARC server accordingly we need use the endpoint for storage we have to use “storage.azure.com” and for vault it will be “vault.azure.net”
CHALLENGE_TOKEN_PATH=$(curl -s -D – -H Metadata:true “http://127.0.0.1:40342/metadata/identity/oauth2/token?api-version=2021-02-01&resource=https%3A%2F%2Fstorage.azure.com%2F” | grep Www-Authenticate | cut -d “=” -f 2 | tr -d “[:cntrl:]”)
CHALLENGE_TOKEN=$(cat $CHALLENGE_TOKEN_PATH)
if [ $? -ne 0 ]; then
echo “Could not retrieve challenge token, double check that this command is run with root privileges.”
else
curl -s -H Metadata:true -H “Authorization: Basic $CHALLENGE_TOKEN” “http://127.0.0.1:40342/metadata/identity/oauth2/token?api-version=2021-02-01&resource=https%3A%2F%2Fstorage.azure.com%2F”
fi
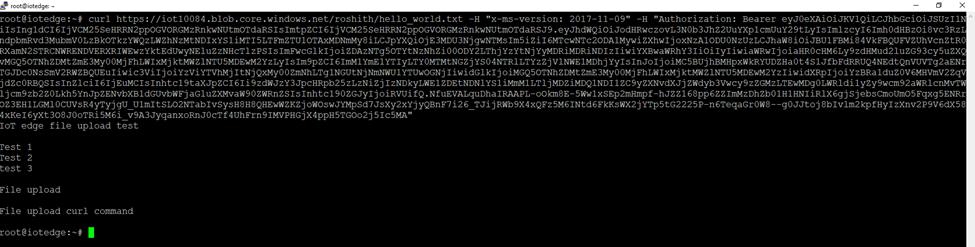
Access the files using curl commands.
We have uploaded a txt file on https://iot10084.blob.core.windows.net/roshith/hello_world.txt
And we can validate the file using curl commands.
Curl command to check the file contents.
curl https://iot10084.blob.core.windows.net/roshith/hello_world.txt -H “x-ms-version: 2017-11-09” -H “Authorization: Bearer eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsIng1dCI6IjVCM25SeHRRN2ppOGVORGMzRnkwNUtmOTdaRSIsImtpZCI6IjVCM25SeHRRN2ppOGVORGMzRnkwNUtmOTdaRSJ9.eyJhdWQiOiJodHRwczovL3N0b3JhZ2UuYXp1cmUuY29tLyIsImlzcyI6Imh0dHBzOi8vc3RzLndpbmRvd3MubmV0LzBkOTkzYWQzLWZhNzMtNDIxYS1iMTI5LTFmZTU1OTAxMDNmMy8iLCJpYXQiOjE3MDU2ODA4MjgsIm5iZiI6MTcwNTY4MDgyOCwiZXhwIjoxNzA1NzY3NTI4LCJhaW8iOiJFMlZnWUFpUWVkYnBkbkdLc09pRkF4TjVaSlZYaVYvZFdCOGtYTW84KzlrVTlzd1Vkd1lBIiwiYXBwaWQiOiJkMDM1ODk5Ni03M2FmLTQ4NjYtOGNjNi02NjIwNGIwNGI0MjMiLCJhcHBpZGFjciI6IjIiLCJpZHAiOiJodHRwczovL3N0cy53aW5kb3dzLm5ldC8wZDk5M2FkMy1mYTczLTQyMWEtYjEyOS0xZmU1NTkwMTAzZjMvIiwib2lkIjoiYzViYTVhMjItNjQxMy00ZmNhLTg1NGUtNjNmNWU1YTUwOGNjIiwicmgiOiIwLkFSOEEwenFaRFhQNkdrS3hLUl9sV1FFRDg0R21CdVRVODZoQ2tMYkNzQ2xKZXZFZkFBQS4iLCJzdWIiOiJjNWJhNWEyMi02NDEzLTRmY2EtODU0ZS02M2Y1ZTVhNTA4Y2MiLCJ0aWQiOiIwZDk5M2FkMy1mYTczLTQyMWEtYjEyOS0xZmU1NTkwMTAzZjMiLCJ1dGkiOiJ2WW5zTFVVdDZrNkRrMldGRnRraUFBIiwidmVyIjoiMS4wIiwieG1zX21pcmlkIjoiL3N1YnNjcmlwdGlvbnMvM2JmMjM0OTItYTVkMS00M2VhLWIyYzUtOWMwNmIwNDU0MjVkL3Jlc291cmNlZ3JvdXBzL3NkYzMtMTAwODQtZGV2LXJnL3Byb3ZpZGVycy9NaWNyb3NvZnQuSHlicmlkQ29tcHV0ZS9tYWNoaW5lcy9pb3RlZGdlIiwieG1zX3RkYnIiOiJFVSJ9.rCaw6mHd0JB4siUeIpG6tLMr18hSZHER3j0sBxnSLlKKbuhsZWBk34gJV2y5iGhTcUvC6-Wn9W1f3ccfDqx407hF3VyYDtiEudvimHyX1p8I1rXxHJbfOzvl-ebmTg-AY6mva0PMl6vHU2gY-bNqvDsQ3taWmWdEsJ8H-4H8KZ2ejQGl-AXNZsMMhFQ2TYYvctO7bjz7o6-jWvElFa93tL1qfCe49M8AIpbFSzTQPhDqjsuvjBg0YmgKgUv2CRf3FwMkBMvXn2FqrwQ6P0F2NK9n8wRj5YuoBfA1zcIb5GAprGIyH6ZzobdFYUzQgrgk6X4kpeITYum-_st0JpKa1Q”
Result :-
Steps to upload the files to storage account using REST API
Create a text file using vi command use below commands to upload the files to storage account.
Sample command
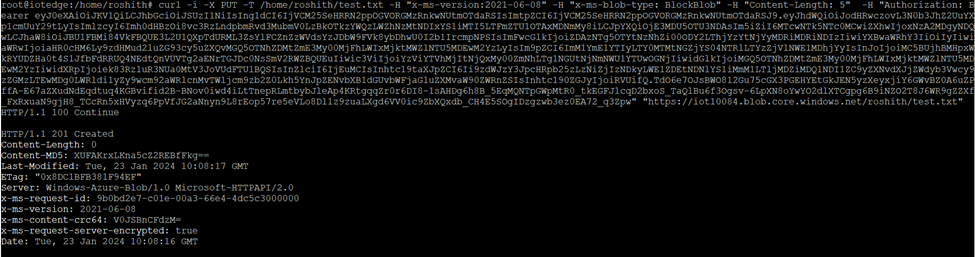
curl -i -X PUT -T /home/roshith/test.txt -H “x-ms-version:2021-06-08” -H “x-ms-blob-type: BlockBlob” -H “Content-Length: 5” -H “Authorization: Bearer eyJ0eXAiOiJKV1QiLCJhbGciOiJSUzI1NiIsIng1dCI6IjVCM25SeHRRN2ppOGVORGMzRnkwNUtmOTdaRSIsImtpZCI6IjVCM25SeHRRN2ppOGVORGMzRnkwNUtmOTdaRSJ9.eyJhdWQiOiJodHRwczovL3N0bXXXXXXXXXX1OTAxMDNmMy8iLCJpYXQiOjE3MDU5OTU3NDAsIm5iZiI6MTcwNTk5NTc0MCwiZXhwIjoxNzA2MDgyNDQwLCJhaW8iOiJBU1FBMi8XXXXXXXXXXk8ybDhwU0I2b1IrcmpNPSIsImFwcGlkIjoiZDAzNTg5OTYtNzNhZi00ODY2LThjYzYtNjYyMDRiMDRiNDIzIiwiYXBwaWRhY3IiOiIyIiwiaWRwIjoiaHR0cHM6Ly9zdHMud2luZG93cy5uZXQvMGQ5OTNhZDMtZmE3My00MjFhLWIxMjktMWZlNTU5MDEwM2YzLyIsIm9pZCI6ImM1YmE1YTIyLTY0MTMtNGZjYS04NTRlLTYzZjVlNWE1MDhjYyIsInJoIjoiMC5BUjhBMHpxWkRYUDZHa0t4S1JfbFdRRUQ4NEdtQnVUVTg2aENrTGJDc0NsSmV2RWZBQUEuIiwic3ViIjoiYzViYTVhMjItNjQxMy00ZmNhLxxxxxxxxxNDkyLWE1ZDEtNDNlYS1iMmM1LTljMDZiMDQ1NDI1ZC9yZXNvdXJjZWdyb3Vwcy9zZGMzLTEwMDg0LWRldi1yZy9wcm92aWRlcnMvTWljcm9zb2Z0Lkh5YnJpZENvbXB1dGUvbWFjaGluZXMvaW90ZWRnZSIsInhtc190ZGJyIjoiRVUifQ.TdO6e7OJsBWO812Gu75cGX3PGEHYEtGkJEN5yzXeyxjiY6GWvBZ0A6uZPffA-E67aZXudNdEqdtuq4KGBvifid2B-BNov0iwd4iLtTnepRLmtbybJleAp4KRtgqqZr0r6DI8-1sAHDg6h8B_5EqMQNTpGWpMtR0_tkEGFJlcqD2bxoS_TaQlBu6f3Ogsv-6LpXN8oYwYO2dlXTCgpg6B9iNZO2T8J6WR9gZZXf_FxRxuaN9gjH8_TCcRn5xHVyzq6PpVfJG2aNnyn9L8rEop57re5eVLo8Dl1z9zuaLXgd6VV0ic9ZbXQxdb_CH4E5SOgIDzgzwb3ez0EA72_q3Zpw” “https://iot10084.blob.core.windows.net/roshith/test.txt”
Result:-